Software security has always been misconstrued as IT Security. Whenever people are asked “is your software secure?”, the reaction is “we have a firewall”. Well, it is high time for people to become more knowledgeable!
With the advent of digital age, when all, well almost all, software applications are on the web and mobile. This leads to applications falling prey to attacks from various corners where people are continuously sniffing for such vulnerable software.
Many enterprises also work with a false comfort that ‘my application is not external facing and thereby not prone to attacks’. OWASP – the most popular online security community – tells that many of internal facing application also has been prone to attacks, often more than what is thought of.
It would not be long that few odd sounding cyber news would start becoming Headlines across the globe. My creative mind is suggesting some possibilities below:
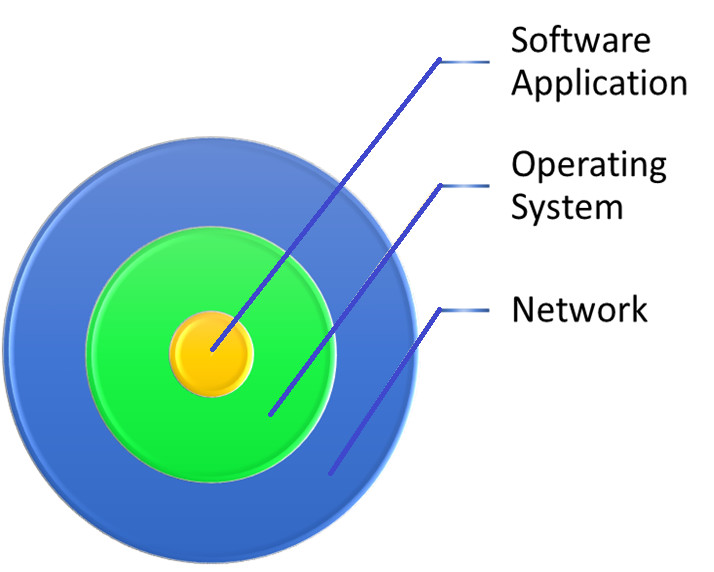
The security architecture
Attacks to software application happen after the network and the operating system has given way – this is in the simplest form.
Security threat modelling – the start
It is important to do security threat modelling before we jump into security review of the source code. While threat modelling is primarily to safeguard enterprise interests, it more should look from attackers mindset than defenders mindset.
It goes beyond this post’s scope of describing threat modelling, but entities like OWASP have got resources that could help in doing effective threat modelling. Security threat modeling should consider the following:
- Sources of threats
- Attack surface – defined through the application internal and external interfaces
- Possible attacks – where can the salvo be served from
- Potential business/technical impacts
- Required controls – this is decided based on organisation’s risk appetite
Cyber security market ventures project an expenditure of US$1trillion on cybersecurity initiatives from 2017 to 2021.
Build the right team
It is important that you build the right team to secure your software applications. Right people are the ones who have got expertise in thinking creatively about how an attacker can damage, and implement controls. It is not the technical skill alone that makes a person a good security auditor/reviewer, but the ability to understand the business context and review the application matters most.
Just a small addendum, DevOps stresses on the security of the application and there is a new branch of it called DevSecOps that is becoming strong. Software security is a moving target, what was strong yesterday is fully vulnerable today, and that’s the fun in it.
Written by Ramkumar Ramachandran, Director & CIO at Tevel Cyber Corps




