Threat modelling is too much of a sophisticated term, but the message is to tell how connected cars can be impacted from the outside world. Every threat analysis primarily focuses on two parameters:
- Channels that could create damage
- Actors who could use these channels
With the advent of technology and need to be connected to the net, the channels of intrusion in connected cars are plenty. The image below depicts few of them:
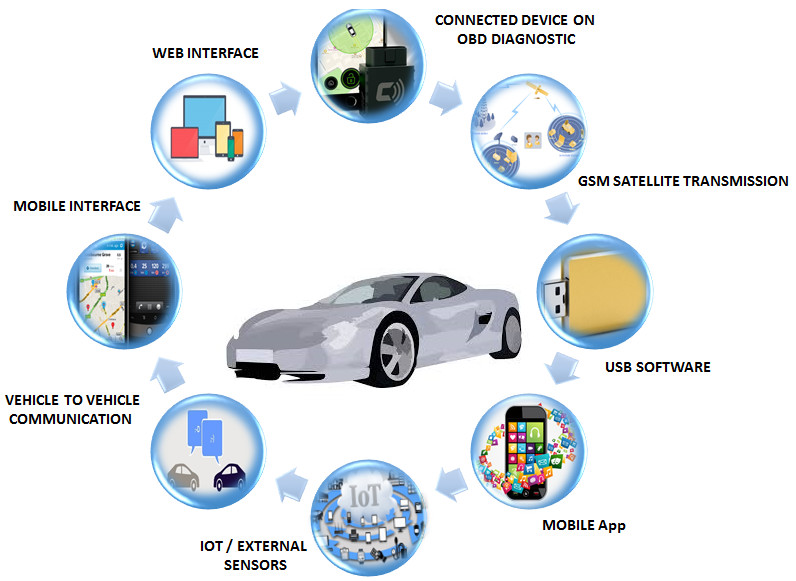
The actors who would take charge of the above channels to create trouble would be:
- Proximity-based access
- Internet access
- Mobile devices
- Malicious media
- Hostile intents etc.
So, the total possible attacks on a car is a product of channels and actors who want to use these channels. Just remember, the fancy of this attack is that you may not know that your car is being compromised unless it is on those brakes or air-conditioning or jarring sounds of a music system.
Configuration change
The fact of life is that there is literally nothing of the above channels that a sophisticated car owner would want to do away for the fear of security. Unless you run the age-old sedan where the highest sophistication you have is ‘auto-fuel-lid-opener’.
When the WIRED Magazine published the Jeep Cherokee compromise done by Charlie Miller and Chris Valasek, people did not want to believe it. It was an eye-opener for many car manufacturers that has led to new cybersecurity initiatives. Well, in hindsight all of these were only waiting to happen.
While these compromises can be fixed through patch update, configuration change or new installation, none of these happen in real-time. The new legislation called Security and Privacy in Your Car (SPY Car Act) demands protection against digital attacks and restrict what data is collected by vehicles sold in the US. Yet, it is a way to go for a truly secured car running on the streets.
Connected car security
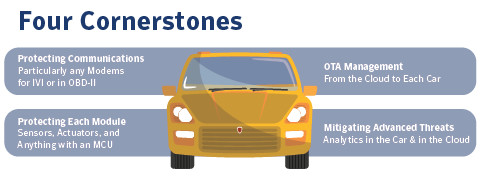
Symantec Corp tells that it would take years to build comprehensive security requires building security into the car at each layer. Some of the layers that the cars have today are:
- Cloud-based OR the data centre systems that cars connect
- The connection itself.
- Multiple modules viz. single board computer (SBC), body control module (BCM), sensor modules.
Popular attacks
Some of the popular attacks through the channels listed above are:
- GSM transmission of telematics unit which was not properly secured allowed to take over the car remotely. Look at the BMW case here.
- Malicious audio played on car’s audio could alter the firmware and create an entry point for attackers.
- Cars opening up for communications in vehicle-to-vehicle and vehicle-to-infrastructure interactions a Pandora’s box could open up through unscrupulous elements
- Wireless key entries which work on proximity and few related parameters are one of the heavily compromised sources
- External Sensors could be spoofed to make the car take wrong decisions. Here is one study on Tire Pressure Management System that talks about vulnerabilities.
Helping secure vehicles
Some of these standards are applicable across industries, while some are aimed primarily on automobile industry:
■ ISO/IEC 9797-1: Security techniques – message authentication codes.
■ ISO/IEC 11889: Trusted platform module.
■ ISO 12207: Systems and software engineering – Software life cycle processes.
■ ISO 15408: Evaluation criteria for IT security.
■ ISO 26262: Functional safety for road vehicles.
■ ISO 27001: Information security management system.
■ ISO 27002: Code of practice – security.
■ ISO 27018: Code of practice – handling PII / SPI (privacy).
■ ISO 27034: Application security techniques.
■ ISO 29101: Privacy architecture framework.
■ ISO 29119: Software testing standard.
■ IEC 62443: Industrial network and system security.
Comprehensive standards
Comprehensive standards SAE International has published OR WIP are:
■ J2945: Dedicated short-range communication (DSRC) minimum performance requirements.
■ J3061: Cybersecurity guidebook for cyber-physical vehicle systems.
■ J3101: Requirements for hardware-protected security for ground vehicle applications
Security for connected cars are still evolving and would take a long time to mature. Maturing will be fastened with the advent of more mishaps and bad experiences of customers. Read this material for a very interesting and in-depth understanding on how cars can be remotely hijacked (related to the video above).
It’s a fascinating game of multiple rounds. First-round hackers win and then the car makers and then the hackers and then the car makers…! The game will keep going on till one of them gets tired…! (And that’s impossible…!)
Written by Ramkumar Ramachandran, CIO, Tevel Cyber Corps Private Limited




